Managing previously unseen levels of capacity and support for up to tens of millions of user connections per second is mandatory for virtual business. Our Managing Director Chandran Dharani is a Master of Science in Engineering in Computer Applications from California State University USA.

Nse4 5 4 Exam Dumps A Fortigate Is Configured With The 1 1 1 1 24 Address On The Wan2 Interface And Https Administrative
AdSecurity Kerberos GT Aug 2015 If a domain within a forest is untrustworthy then it should not be a member of the forest.

Within the age of data specializing in fortigate ssl vpn. A policy or a program that seeks to redress past discrimination through active measures to ensure equal opportunity as in education and employment. SSL. Applying SID Filtering to domain trusts within a single forest is not recommended as it is an unsupported configuration and can cause breaking changes.
Starting from the analysis of modern high-performance SAN platforms the course describes the most important features including the direct communication with the hypervisor the mechanisms of Fast Replication Smart Caching and Data. The FortiGate unit has a choice of modes that it can be used in either NATRoute mode or Transparent mode. To develop industry in a country or society for example.
EDR means Endpoint Detection Response and that means that the age of AI is upgrading networks. The FortiGate unit is able to operate as a firewall in both modes but some of its features are limited in Transparent mode. Previously he was a Security Product Manager at F5 specializing in network security Governance Risk and Compliance GRC.
No Data Retention - Full Anonymity. Support access and manage all devices for customers. Protect your employees data and passwords wherever they work.
Our management comprises of technical people. For 87000 FortiGate SSL VPN. Ad The 1 VPN Service for Singapore.
Academiaedu is a platform for academics to share research papers. The first CVE20195701 is a problem within GameStream. As VPN services rely on user trust and data.
Ad The 1 VPN Service for Singapore. These credentials were obtained from systems that remained unpatched against. Big Data training can help you acquire the knowledge of infrastructure equipment and software used by Storage Area Networks in this Big Data era.
FREE Economics Vocabulary Crossword Puzzle Answers. The first part is to identify where you want to send it. He joined F5 in 2010 as a Security Architect and was responsible for designing F5s current Information Security Management System ISMS.
High-velocity e-retail and e-commerce providers handling event-based connection bursts. It is always best to choose which mode you are going to be using at the beginning of the set up. Multi-Platform Capability Our docks work with Mac and PC platforms as well as with Chrome OS Android and Linux.
When enabled an attacker with local access can load Intel graphics. With a Security Compute Rating of 5x for SSL inspection including TLS 13 FortiGate 4200F delivers the industrys best priceperformance. The vulnerability was isolated to three small payment providers and possible to exploit only within a.
Three vulnerabilities have been resolved in GeForce Experience. SentinelOne is a cyber intelligence company specializing in safeguarding endpoints through innovations in artificial intelligence and machine learning. Network security solutions provider Fortinet confirmed that a malicious actor had unauthorizedly disclosed VPN login names and passwords associated with 87000 FortiGate SSL-VPN devices.
No Data Retention - Full Anonymity. Some of the applications are hosted at our data center with firewall and secured VPN with SSL. Security team analyzes data breach costs for better metrics Black Hat USA 2020 Severski and Baker published their findings on the cost of data breaches in the Cyentia Information Risk Insights Study IRIS 2020 and the ripple effects of breaches in Ripples Across the Risk Surface in collaboration with automated risk assessment firm RiskRecon.
Intuitive secure personal password manager available on any device. Akamai is the leading content delivery network CDN services provider for media and software delivery and cloud security solutions. All computers as well as routers have an IP address that is a series of four numbers between 0 and 255 and separated by periods such as 192005 note that this is an IPV4 address.
Microsoft Netdom Trust Sept 2012 Citation. This broad compatibility supports flex working applications like hoteling and hot-desking and provides a future-proof solution that eliminates the need for replacement during. Simple safe password management and sharing for your entire family.
Effortless password security management and sharing for employees working from anywhere. Data Packets After you have established a connection whether it is physical or wireless you need to send data.

Fortinet Communication Ports And Protocols Fortigate Fortios 6 0 0 Fortinet Documentation Library Communication How To Be Outgoing Port

Fortiscan Fortigate Ssl Vpn Vulnerability Scanning And Exploitation Tool

Handbook Fortigate Fortios 6 0 0 Fortinet Documentation Library

Fortigate 7000 Handbook Fortigate 7000 6 0 8 Fortinet Documentation Library

New Features Fortigate Fortios 6 4 0 Fortinet Documentation Library

Handbook Fortigate Fortios 6 0 0 Fortinet Documentation Library

Fortigate 6000 Handbook Fortigate 6000 5 6 11 Fortinet Documentation Library

New Features Fortigate Fortios 6 4 0 Fortinet Documentation Library

Administration Guide Fortigate Fortios 7 0 1 Fortinet Documentation Library
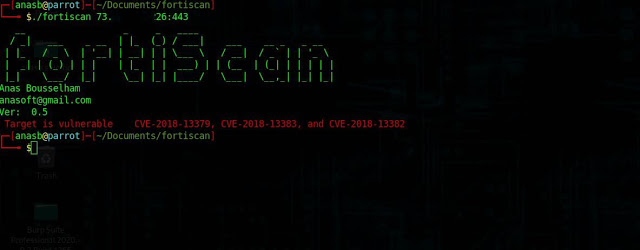
Fortiscan Fortigate Ssl Vpn Vulnerability Scanning And Exploitation Tool

Cookbook Fortigate Fortios 6 2 0 Fortinet Documentation Library
Https Fortinetweb S3 Amazonaws Com Docs Fortinet Com V2 Attachments De1e129a 0283 11ea 8977 00505692583a Fortios 6 4 0 New Features Guide Pdf

Administration Guide Fortigate Fortios 6 4 4 Fortinet Documentation Library

Cookbook Fortigate Fortios 5 4 0 Fortinet Documentation Library

Fortigate High Availability Ha Manualzz

Handbook Fortigate Fortios 6 0 0 Fortinet Documentation Library

Handbook Fortigate Fortios 6 0 0 Fortinet Documentation Library

Fortinet Fortigate Ec2 Auto Scaling On Aws Quick Start
No comments:
Post a Comment