Apply that to your 3rd party-CA Comondo. I also am not a fan of the FortiGate VPN wizard so this module just made sense.

Oops There Was A Problem Displaying This Page In 2021 Clear Browsing Data Grammar Errors Digital Marketing Services
Set Listen on Port to 10443.

Fortigate ssl vpn certificate. The CSR and Private Key form the SSL certificate key pair. Log into your FortiGate Management Console. Go to VPN Certificates Local Certificates and hit Generate.
When i try to choose the certificate from Forticlient SSL VPN setting it is not showing the installed certificate from. There are a few different reasons why you may want to install an SSLTLS certificate on FortiGate for example it could have to do with wanting to secure your communications via a virtual private network VPN. Enable Client Certificate and select the authentication certificate.
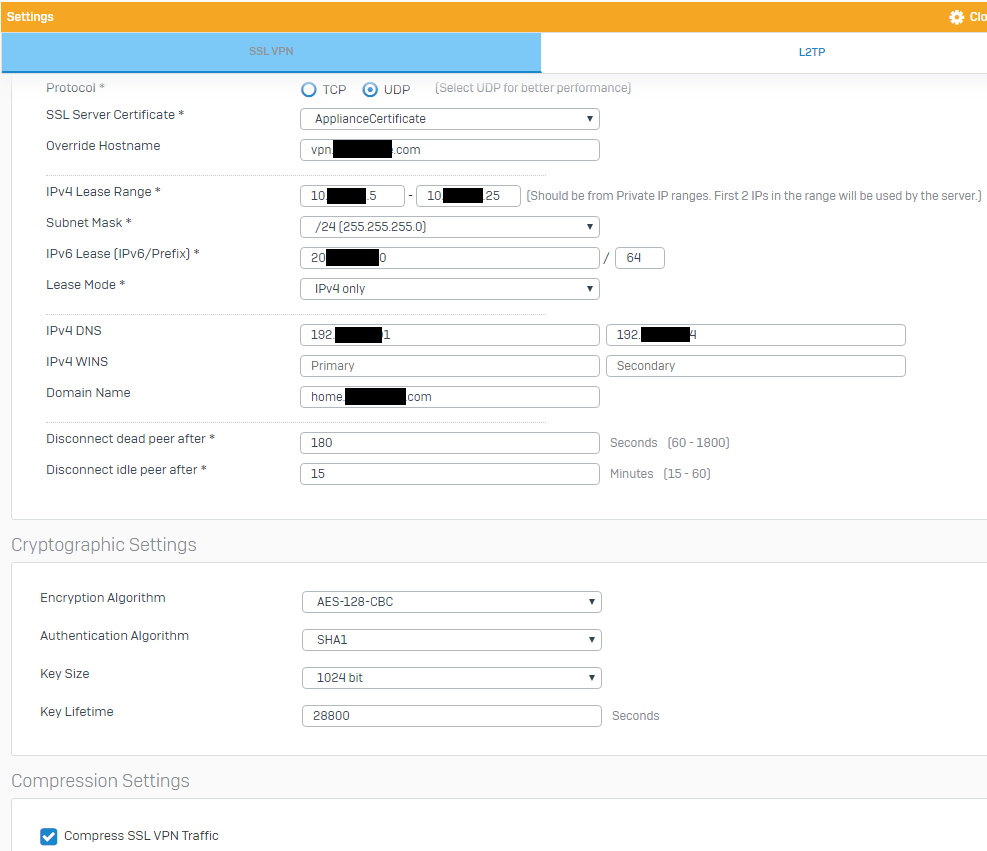
Go to VPN SSL-VPN Settings. This article will go into detail on how to install certificates on Fortigate SSL VPN. Set Server Certificate to the authentication certificate.
Install the server certificate. Purchasing an SSL certificate package from a Certificate Authority CA. Configure SSL VPN settings.
Generate the CA or root certificate Certificate Authority You will need to generate a root certificate to sign the Server and Client certificate. Disable Enable Split Tunneling so that all SSL VPN traffic goes through the FortiGate. This portal supports both web and tunnel mode.
Give a friendly name to your CSRPrivate key files. The CA certificate is available to be imported on the FortiGate. Go to VPN.
Client certificate is installed in root certificate folder. Once cert is generated. Forticlient SSL VPN doesnt show the certificate to select Hi I would like to implement SSL VPN with certificate authentication.
The CSR need to be provided to a Certificate Authority CA for signing and the private key will remain hidden on the FortiGate system where the CSR request is made. To generate the CSR code on FortiGate please follow the steps below. I have configured SSL VPN with PKI users and CA certificate is uploaded to Fortigate.
Select Customize Port and set it to 10443. Once you have purchased your certificate and the domains have been validated as under your ownership you will receive an email containing the certificateOnce you receive your certificate issuance ZIP file extract the files contained in the ZIP file to the server. You generate a CSR.
Go to VPN SSL-VPN Settings. Heck you may even be one of them. 2 Connect to the FortiGate unit via SSH to import the new signed certificate config vpn certificate local edit certificate name.
To configure SSL VPN in the GUI. Configure SSL VPN web portal. Here are the five steps.
Go to VPN SSL-VPN Portals to edit the full-access. Send CSR to your CA for signing and to generate Certificate file. The SSL VPN certificate is just like a Web server certificate.
To generate a Certificate Signing Request CSR for FortiGate SSL VPN you will need to create a key pair for your server the public key and private key. The server certificate allows the clients to authenticate the server and to encrypt the SSL VPN traffic. We will be using OPENSSL to generate the CA and certificates.
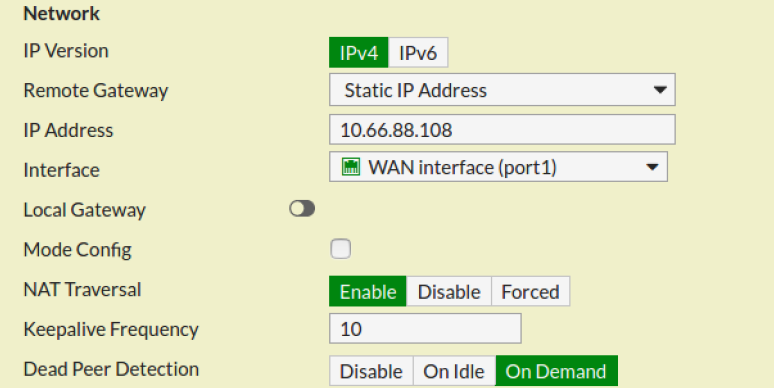
Configure SSL VPN settings. This is a detailed guide on how to configure a SSL VPN with certificate authentication on a Fortigate. L Set Remote Gateway to the IP of the listening FortiGate interface in this example.
Then import the answer file CER. Log into your FortiGate Management Console. Note that regardless of certificates file extension the certificate must be PEM encoded not DER encoded.
Select the Listen on Interface s in this example wan1. So without wasting much time lets get straight to the SSL Installation procedure in FortiGate. FortiGate SSL VPN with machine certificate only authentication Hi rfortinet Im trying to configure FortiClient SSL VPN 642 with a FortiGate 624 for machine cert only authentication.
To generate the CSR code on FortiGate please follow the steps below. INSTALLING A NEW SSL-VPN CERTIFICATE To Renew Certificate see separate article here Go back to Certificates page Highlight the new Certificate Name you just created and click download. Installing SSL Certificate for SSL-VPN Guide.
Fundamentally any SSL installation process can be divided into five steps and FortiGate is no different. On the Generate Certificate Request page submit the following information that applies to you. How to install a wildcard SSL certificate on a FortiGate is a topic that pops up in conversation with our customers once in a blue moon.
Choose proper Listen on Interface in this example wan1. If it is DER encoded you will not see the words BEGIN CERTIFICATE or END CERTIFICATE. Disable Enable Split Tunneling so that all SSL VPN traffic goes through the FortiGate.
The CA has issued a server certificate for the FortiGates SSL VPN portal. L Set VPN Type to SSL VPN.