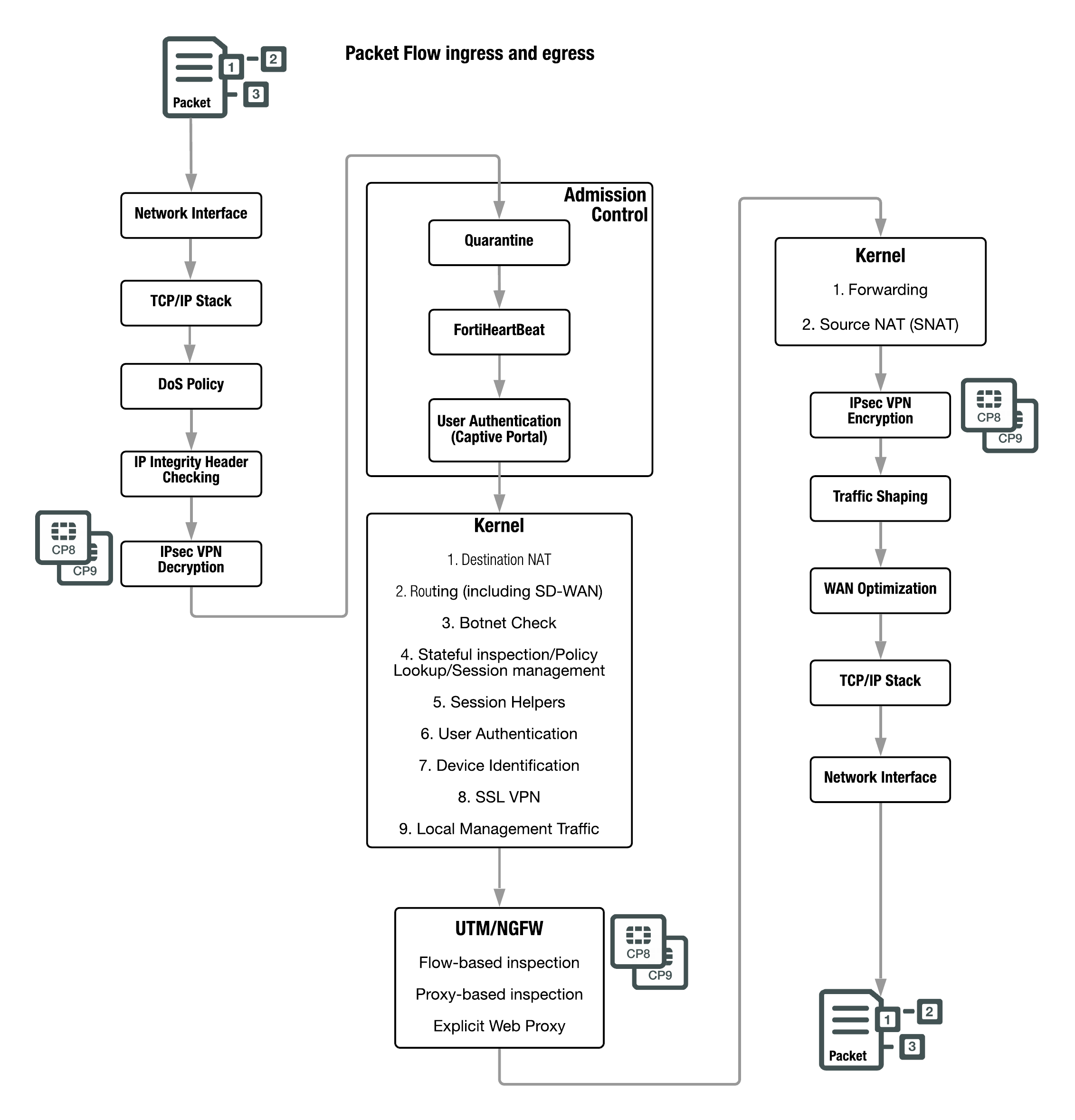
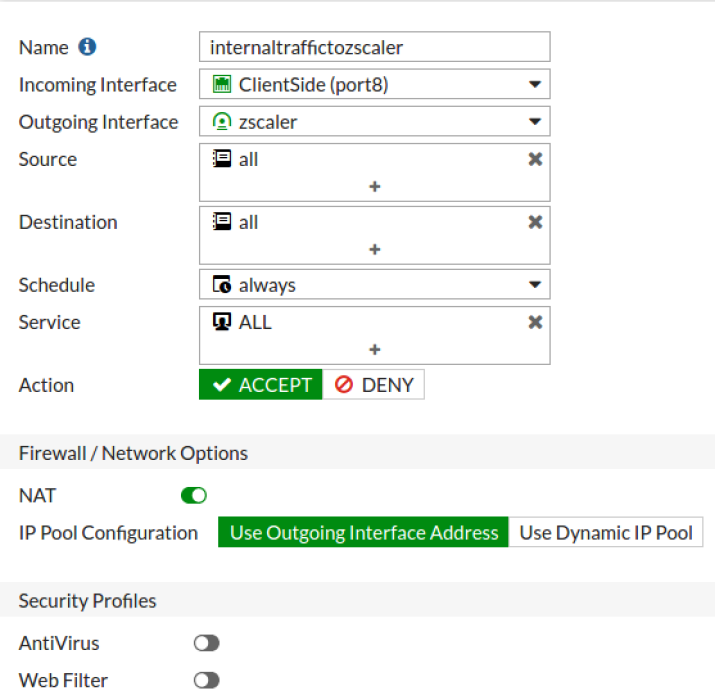
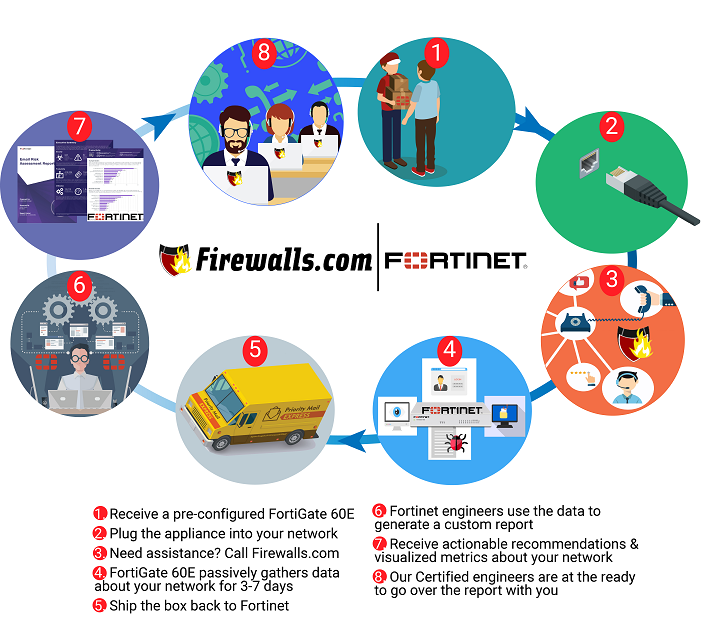
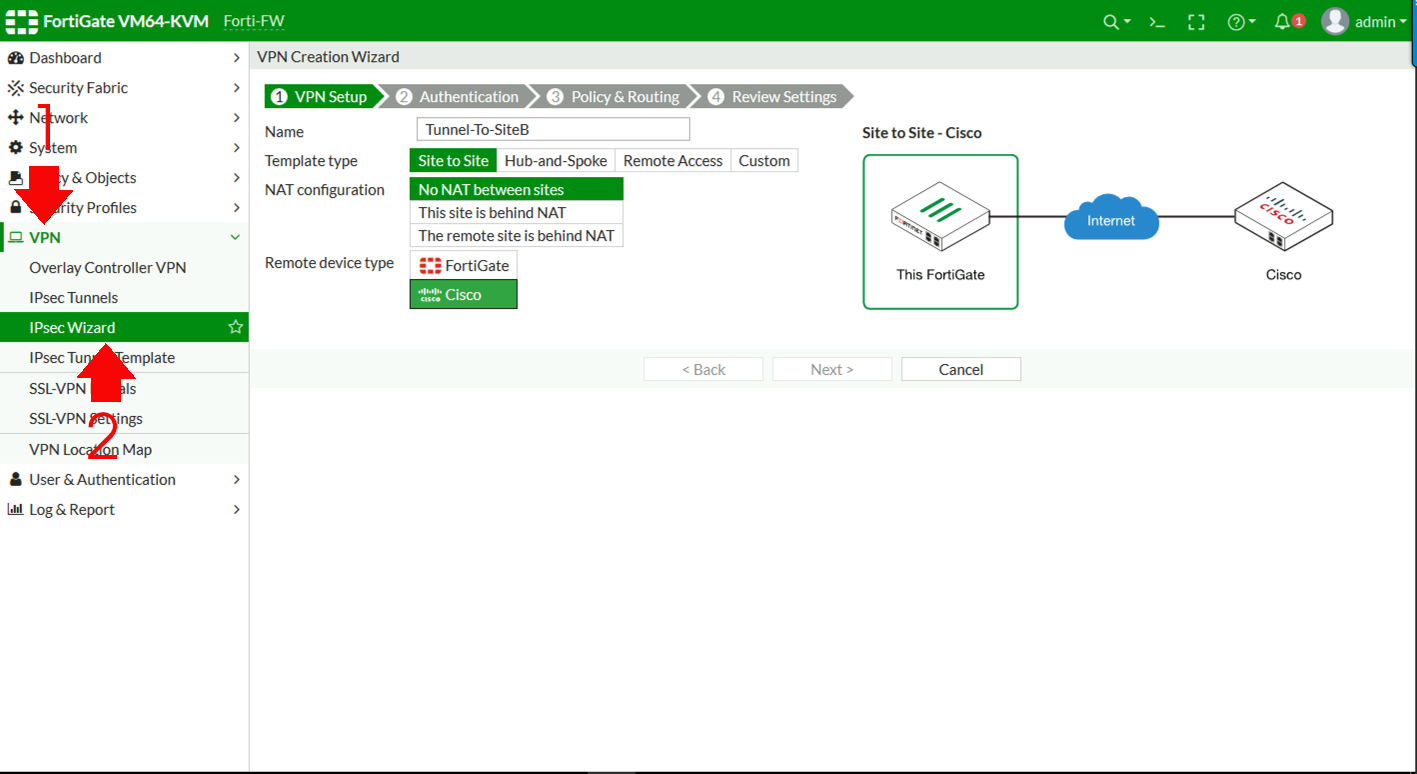
Pending you have previously been using the ATT modem as a router before trying to install the FortiGate UTM Firewall you will need to connect to the IP of the uVerse router. In this image the remote Fortigate represents Azure cloud the customer servers are located there.

Ssl Certificate Web Services Dealer Price Mumbai India Ssl Certificate Ssl Digital Certificate
O serviço gratuito do Google traduz instantaneamente palavras frases e páginas da Web entre o inglês e mais de 100 outros idiomas.

Dont just sit there start getting more fortigate utm. I am getting ready to box up and ship it out. So you should count the 60E as a 175Mbps UTM firewall - thats the rate. For example I just set up a new network with a 100E and I have got four stackable switches.
-block webmail for other various reasons - Standard virus scanners etc. It has to be simple for the client to use and simple for us to install on their Home dodgy PC with spyware preloaded and 1000 games that their 10 years son plays and wont get off it I digress. Depends on you needs.
But last week we change our IP from our site to the countyI work at a school district. There is no difference in managementrestore as each UTM emails its config out each night so restoring a fresh appliance to production takes literally 30 seconds from it powering on. Guys I am experiencing a bit of an issue.
Fortinet FortiGate Mid-Range Solutions To be effective against todays evolving threat landscape your security solution needs to reliably control network traffic through awareness of applications users and content FortiGate-110C FortiOS 30 MR6 Install Guide 6 01-30006-0481-20080728 About the FortiGate-110C Introduction About the FortiGate-110C The FortiGate-110C is an ideal solution for. Works with any internet capable device. Find out how Palo Alto Networks next-generation Prisma SD-WAN can help your organization embrace the cloud.
It will run a network with 23 access points. It wont take more than four hours of work. 707854 FortiGate is not able to resolve FQDNs without DNS suffix for firewall address objects.
But if youre using multiple routers you can get a hardware UTM which acts as a portal for all your office routers. - Block all downloadable exes msis zip docs excel etc unless its from an approved websites plus our UTM proxy blocks from phishing websites and bad reputation sites-Users are only users on the computers. Basically here are the steps.
I only have one physical port available on each of the Fortigates so am trying to make use of VLANs. In this image the local Fortigate represents the customer on site Fortigate. 709832 When there are multiple internet services configured that match a certain IP port or protocol it may cause the wrong policy to be matched.
Prisma SD-WAN Integrated with AWS Transit Gateway Connect. To find this open a command prompt and type ipconfig The. I cant ping our gateway but not sure if that is normal from inside.
By consolidating your firewall protection in the UTM device you can get in-depth protection from cybersecurity threats across your entire local networkwithout having to change the settings on each. I have two Fortigate 1000A s that I am trying to connect over a L2 circuit. No neither UTM device or plain routers are in or on the way out they both target different needs.
I set up all the VLANs routing rules and other things. If you feel the need for a Unified Threat Management box then go ahead and get one. There are a lot of UTMs on the market and each UTM is a little different.
We use Fortigate for now and have been for the last 4-5 years. PPTP L2TP OpenVPN Support. Whether youre looking for hotels homes or vacation rentals youll always find the guaranteed best price.
When it comes to SD-WAN legacy solutions are falling behind. Any give me any advice. Encrypt and secure your internet traffic.
Browse our 2563380 accommodations in over 85000 destinations. Hi all Im new to Fortinet and this position. But I just noticed the VPN stopped working.
Local LAN is port 3. I dont know where to start. Access all Smart DNS Proxy services while you are connected to any SmartVPN server.
I have created the VLAN on each of the interfaces Int 8. The newest of these protocols. The Utmevent VPN threat disconnect present have apps for just about every twist Windows and Mac PCs iPhones Android devices Smart TVs routers and more and while they might uninjured complex its straightaway every bit undemanding territory pressing a single button and getting connected.
It is pretty simple. No PPTP as its just a username and password system like RDP and more passwords to remember. Unblock websites digital media with the fastest way.
It has two internet connections port 1 and port 2. But you still need to have an eye on the IPS throughput. In most cases the firewall throughput is more than big enough when you initially picked a high enough UTM throughput.
Server load-balancing on FortiGate is not working as expected when the active server is down. Yes we have pretty high levels of resiliency and failover in our VM hosting but having the appliance separate means we keep the two most vital pieces of infrastructure separate in case of maintenance needs. However when I pa.