Of course there are many more tips for securing your apps servers but these 15 best practices should be enough to keep you safe in most situations. Create a remote access SSL VPN with the legacy client.

Security Tips And Statistics Each Of Us Uses Wi Fi Networks Regularly In Public P Cyber Security Awareness Cyber Security Education Cyber Security Technology
Best Practices for 2021.

Ssl vpn security best practices. A secure socket layer SSL VPN enables users to connect to VPN devices using a web browser. Virtual private network VPN best practices include researching which vendor matches an organizations needs preparing for surges in use keeping the VPN updated and patched using multi. Find content updated daily for vpn in network security.
Safe Secure Trusted Internet Access. Always use a VPN whenever possible to prevent hackers from finding out what youre doing on the web. Make sure that your network security policy is part of the official company manual and that all the employees are given proper overview of the security policy and training for VPN use.
Securing remote access to network resources is a critical part of security operations. In that case you will have to document exceptions to best practices. SSL VPN allows administrators to configure administer and deploy a.
This guide uses the term SSL VPN. Browse privately on up to 10 devices. SSL VPN best practices.
Only on VPN Alliance. Behavior analytics technology lets you detect unusual VPN activity that could represent misuse and respond effectively to minimize or prevent data loss sabotage or other adverse effects to your business. Hi Currently we are authenticating user by below 2 methods please advise that is this sufficient security best practice or do you recommend extra security.
Split tunneling is the capability of a remote router or endpoint to connect to more than one network service. Anyconnect User Authenticate against AAA Radius then in ACS we have configured dACL in user groups to restrict the user access. While security teams should follow best practices to make sure data privacy and security controls are in place they often arent enough to protect your data.
Defining VPN security policies Defining policy addresses. Ad Break down the barriers of internet censorship with a single click. Ad Secure 100 American internet access from anywhere in the world.
1 Corporate User ONLY. See Azure security best practices and patterns for more security best practices to use when youre designing deploying and managing your cloud solutions by using Azure. Ad Looking for vpn in network security.
The VPN establishes an encrypted tunnel to provide secure access to corporate resources. Ad Break down the barriers of internet censorship with a single click. Point-to-site VPN is more secure than direct RDP or SSH connections because the user has to authenticate twice before connecting to a VM.
SSL VPN best practices Basic configuration User accounts and groups Configuring SSL VPN web portals Configuring security policies Configuring encryption key algorithms. SSL VPNs provide remote users with access to Web applications and clientserver applications and connectivity to internal networks. VPN and SSL certificates.
Security management and best practices. No Logs No Names No International Servers. Browse privately on up to 10 devices.
When following the best practices to secure a VPN its important to also understand the associated challenges. This type of VPN may be referred to as either an SSL VPN or a TLS VPN. Find content updated daily for vpn in network security.
Anyconnect SSL VPN best practices. You want to configure and deploy a connection to allow remote users to access a local network. Ad Looking for vpn in network security.
VPN Security Risks. My question to all of you is as far as auditors are concerned do you think they would look at that as a security risk to be using the self signed. SSL VPN device is encrypted with the SSL protocol or its successor the Transport Layer Security TLS protocol.
For example if your local network uses a non-registered domain.

28 Infographs Of Beautiful Data Wow Gallery In 2021 Cyber Security What Is Cyber Security Cybersecurity Hacks

Public Wi Fi How To Secure Your Data In 10 Minutes Asoneforce Public Infographic Wifi
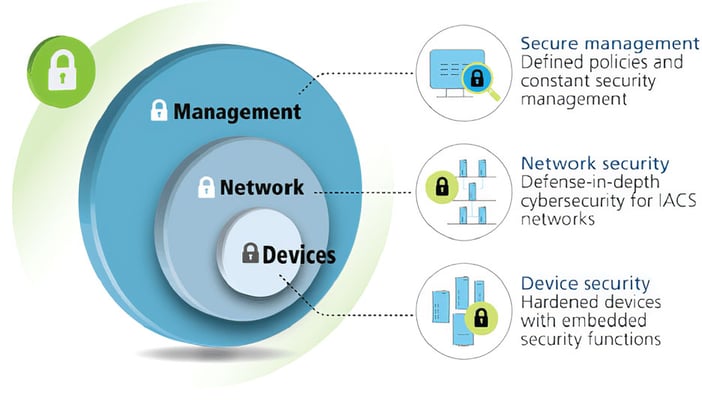
How To Design And Configure Secure Industrial Networks

Microsoft Azure Cloud Security Best Practices N2ws

Protect Yourselt The Dangers Of Identity Theft Online And Offline Infographic Identity Theft Cybersecurity Infographic Online Security

Design Patterns For Microservices Pattern Design Architecture Design

Pin By Mell On Technology Security Architecture Patch Management Data Security

Download Vpn Master Vpn 3 Month Browse The Internet Through Vpn Vpn Vpnnetwork Bestvpn Download Vpn Master Slow Internet Best Vpn Online Traffic

Ssl Tls Client Authentication Know How It Works Ssl Computer Knowledge Ssl Certificate

How To Safely Download Torrents And Protect Your Identity Cyber Security Cyber Safety Lesson Cyber Safety

Aws Security Practices 5 Ways Aws Keeps Your Customer Data Secure Data Security 5 Ways

10 Best Mobile Application Security Best Practices For Developers

Top 10 Internet Security Tips You Won T Want Miss This Read If You Re A Small Business Owner Www Highlyreleva Cyber Security Threats Cyber Security Best Vpn

Benefits Of Local Seo For Your Business Infographic Local Seo Business Infographic Seo

Juniper Network Routers Models Reference Guide Installation Services Freelancers Juniper Networks Ssl Certificate Network Infrastructure

Cci2018 Azure Network Security Best Practices Network Security Networking Connection Network
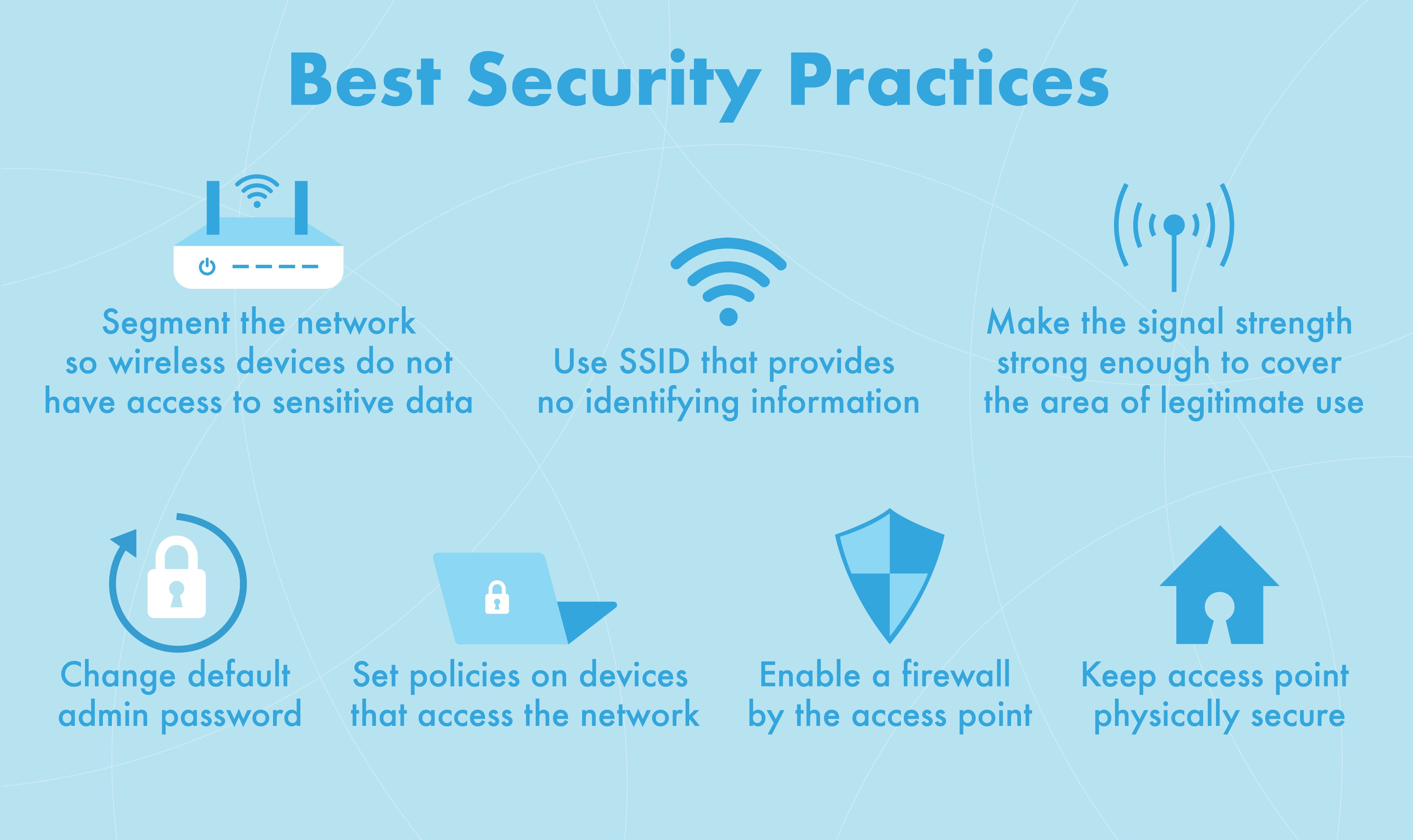
Everything You Need To Know About Network Security

Eight Steps To Iso27001 Certification Infographic Infographic Iso Process Infographics

Phishing Fraud Cyber Security Awareness Computer Security Cyber Security Education
No comments:
Post a Comment