Once you configure High Availability on the Primary SonicWall security appliance you push out the settings to the Backup SonicWall security appliance. Firewalls also Prevent Computer Viruses on Internet gateway level with benefits of.
06c 802 11b G N Router User Manual Sonicwall Tz 210 Series Getting Started Guide Sonicwall
SonicWall Hidden Features and Configuration Options.
Top sonicwall high availability tips. Click Device in the top navigation menu. Find out some other protection tips to. Top 5 Real User.
Right now we run these two connections into two Cisco switches and all of our. Only institution in India with the right blend of theory practical sessions. ActiveActive Clustering High Availability - ActiveActive Clustering is the most recent addition to the High Availability feature set in SonicOS.
Naturally I could use 2 network switches. According to the monitoring settings page the Ip address listed for primary Ip address and secondary Ip address appear wrong. 1 to connect the WANs together and 1 to connect the LANs together.
More than 50000 students trust ACTE. The antivirus and items of that nature were quite helpful to have. Firewall Support Hardware Software Firewall installation configuration and Remote Support Services Customer satisfaction is Firewall Firms s number one priority.
I have a two Sonicwall NSA250Ms where one of them is a high availability device. SonicWall Specialist Expert Advice. Login to the SonicWall management Interface.
SonicWALLs SRA SSL VPN is a highly secure solution with high availability and uptime which is absolutely essential for us. A system that can be run in independent. A typical ActiveActive Clustering deployment includes four firewalls of the same SonicWALL model configured as two Cluster Nodes where each node consists of one Stateful High Availability pair.
The hidden HTML page can be found on all TZ NSA SOHO and various other SonicWALL models. Log Automation E-mail. If you have configured the SonicWALL security appliance to e-mail log files clicking.
The SonicWALL security appliance can alert you of important events such as an attack to. Were adding two SonicWALL NSA 2600 firewalls to our current setup. The sonicwall engineer suggested that I should connect both my WAN and LAN to both of these devices.
Very limited-capability programs running on a low-power CPU system Software firewall appliances. Click Manage in the top navigation menu. I want to connect the routers to the firewalls in such a way that any one device can fail without the whole system losing internet access.
This section provides troubleshooting tips for the following initial. 2 years 224w 231c 231o 3 years 432i advanced advanced edition analytics analyzer essential essential edition hardware high availability nsa2650 nsa2700 nsa3650 nsa4650 nsv reporting secure mobile access secure remote access secure upgrade sma sma 100. In-depth Course coverage for 60 Hours.
SonicWall brings high availability security to mobile business networks Adelle Geronimo November 17 2016 353 pm March 13 2017 SonicWall has announced significant enhancements to its Secure Mobile Access SMA solution providing even greater security to customers in an ever-growing world of everywhere access and BYOD. Whats more with the new spike licensing option we never have to worry about planning for short-term peak usage scenarios if there is ever a need to have more users log in during unexpected emergencies it would be easy for us to handle these short duration. Secondary sonicwall inaccessible.
We have a pair of Sonicwalls in ActiveStandby mode. A firewall is a combo of a firewall software and operating system that is built to run a firewall system on a dedicated hardware or virtual machine which includes. We currently get two WAN connections from two separate Cisco routers running on the same external subnet with what I believe is HSRP.
One of the things that happens frequently when you purchase a new HA pair is that while the units are identical hardware wise one is a HAHigh Availability SKUpart number that does not have the support or security services licenses. Download our free SonicWall NSa Report and get advice and tips from experienced pros sharing their opinions. Once you configure High Availability on the Primary SonicWall security appliance you push out the settings to the Backup SonicWall security appliance.
These settings are not documented and changing settings here could prevent proper operation of the SonicWall. SonicWALL HA w Dual WAN HSRP from two redundant switches. Click the Wizards button at the top right.
Tips for High Availability HA setup. Login to the SonicWall Management Interface. Near the top right corner of the page sends the cu rrent log files to the e-mail address specified in the.
For New HA Pair. Firewall Firms Support Services provide global support for all Configuring Software and Hardware Firewall products and its support services. Page iv SonicWALL TZ 210 Series LED Reference.
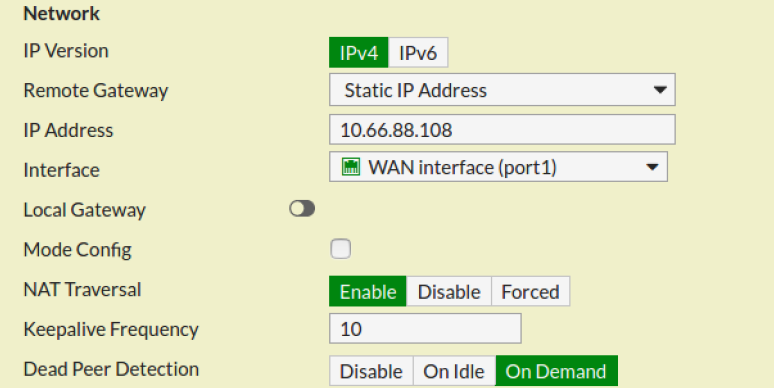
To configure High Availability on the Primary SonicWall perform the following steps. If you do not see the login screen or the Setup Wizard. High availability HA connectivity.
When you enter this configuration page the unit displays the following disclaimerWarning. To configure High Availability on the Primary SonicWall perform the following steps. For example I access the primary sonicwalls web interface via 10002 address and the Primary Ip address listed in the HA monitoring.
I also have two SonicWALL TZ600 firewalls currently configured in Active Standby high availability mode. SonicWall Course in ACTE is designed conducted by SonicWall experts with 10 years of experience in the SonicWall domain.