JAMES GUNN director of hits such as the successful and acclaimed Guardians of the Galaxy and Suicide Squad commented in a recent interview on a number of superhero movies and stated some things that surprised many. The sites may use any RDP software to access it.
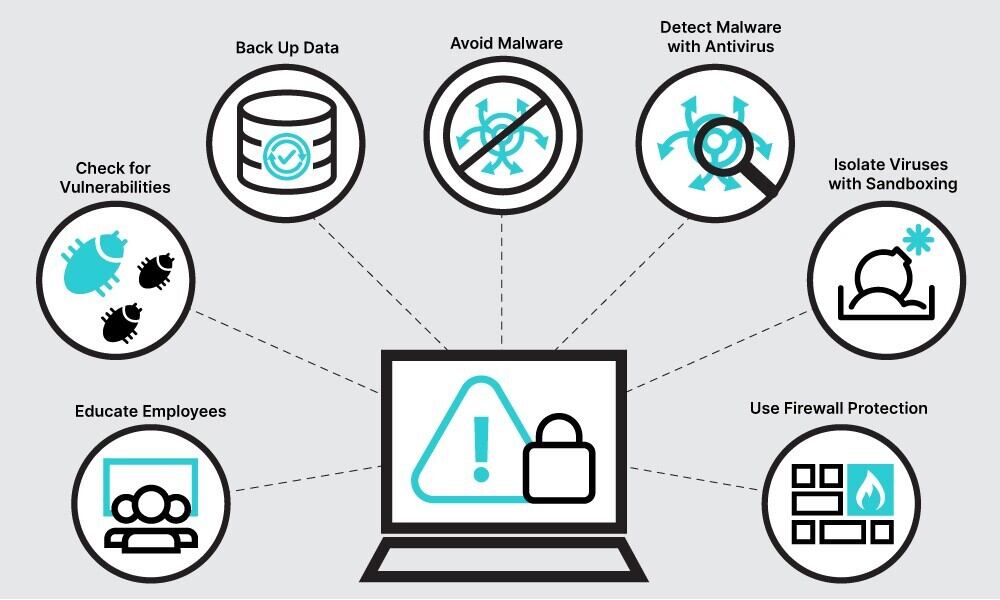
What Is Malware Definition Types How To Guard Fortinet
Now on to the firewall policy configs.

What you dont find out about vpn fortigate may shock you. Make sure to check out our reviews the comments of our users below the reviews as well as the general guideline on What Vpn Do You Use Virtual Private Networks in the Why VPN section. The VPN clientserver of choice is not particularly important I have positive experience with Cisco ASA IPSec tunnels - thats entirely up to your budget. We just got done a web demo with Sophos and liked them but waiting for the sticker shock.
Funny you mention Splunk because that may very well be our syslog server of choice soon. But the leaks dont happen when they are held in secure databases. Step 3 Connect the DB-25 end of the modem.
Config firewall vip edit NameOfVIP set extip 1721611-172161254 set extintf any set mappedip 192168601-19216860254 next. Whetever you buy dont go for a model that covers you capacity of users if you use fullguard. We have Fortinet on deck this afternoon.
Googles free service instantly translates words phrases and web pages between English and over 100 other languages. Browse our 2563380 accommodations in over 85000 destinations. And you do that with command of language.
See bellow this link for sophos sizing. تترجم خدمة Google المجانية الكلمات والعبارات وصفحات الويب بين الإنجليزية وأكثر من 100 لغة أخرى. Whether youre looking for hotels homes or vacation rentals youll always find the guaranteed best price.
NGFWs offer packet filtering virtual private network VPN support support and IP mapping features. If you want What Vpn Do You Use to get a VPN to unblock your favorite streaming What Vpn Do You Use video service like Netflix abroad on your TV another technology might be intersting for you. You need to set the Virtual IP.
You dont need more than one windows instance for that on the server side. VPN is a powerful tool for data protection and online anonymity. The simple answer to the question is.
NGFW providers perform continuous research on the security landscape to learn about new threats as they arise and use this data in the form of automatic updates to block attacks on your devices. You need to reconfigure the firewall policy to accept your DNAT networks. Step 2 Connect the DB-9 end of the console cable to the DB-9 end of the modem adapter.
They happen when it is exported out of its safe environment. In addition you have raw data floating around that may be valuable when analysed such as business forecasts and new business proposals. Make it too simple and you miss out on nuance and configuration options for specific networks that may or may not require ULAs to function or NPTv6 not even Cisco really has it down on anything other than ASRsCSRs and ISRs or NAT66 or how to design an interface that guides you on making firewall rules for remote networks that might still be reachable at least routable due to publically.
Namely as part of the promotion of the new Suicide Squad Gunn told The Irish Times that most modern. Step 1 Connect the RJ-45 end of the adapter cable to the Console port on the router as shown in Figure 3-4. Options may seem well and good online or even in the store but after a month of wearing them they get dirty beyond recognition or you realize that theyre too uncomfortable to wear on a daily basis.
PAN might be 1 and Sophos 1a or 2 right now. Unfortunately I dont have any experience on Fortigate. Palo Alto has learned and embodies a new paradigm in technology.
Please consider the following. You cast your products as the only and create special words like AppID that make your products sound unique and special. To connect a modem to the router follow these steps.
However if you use VPN and Tor together you can protect yourself and make Tor more secure. Dropbox is a modern workspace designed to reduce busywork-so you can focus on the things that matter. You dont need that many white sneakers but theyre a difficult product to vet before buying.
Sign in and put your creative energy to work. If you have the budget a go for 310 or 330. Figure 3-4 Connecting a Modem to the Console Port.
If it is in the VPNs subnet typically 2552552550 for a mask so 254 possible devices you use the VPN gateway instead of the ISP gateway. You dont have to BE innovative you have to make people THINK youre innovative. They also monitor your network keeping an eye out for threats.
This tutorial will show you how you can set up your own VPN server at you home on Raspberry Pi so all your connections on remote devices go through this server as if you were connected to your home Wifi. You can use VPN to browse the Internet safely and reliably anywhere in the world without worrying about hackers spies and malware attacks. First one is easy.
In my case I wanted the spokes to see all 65000. VPN servers are a great way to make sure your connection is secure and safe specially when you are connected to open or shared Wifi network.
Https Pub Kb Fortinet Com Ksmcontent Fortinet Public Current Fortigate Hw Fg 100f Series Qsg Pdf

Vpn Explained How Does Vpn Work And Why Would You Use It

Fortinet Fortigate Reviews And Pricing It Central Station

Fortios Upgrade From 5 4 To 5 6 Issues
Https Pub Kb Fortinet Com Ksmcontent Fortinet Public Current Fortigate Hw Fg 100f Series Qsg Pdf

Fortios Upgrade From 5 4 To 5 6 Issues

Solved Ipsec Vpn Tunnel Between Watchguard And Fortigate Is Up Traffic One Way

Configure Fortigate Ddns With Free Ddns Service Noip Net Infosec Memo
Networking Tips Archives Firewalls Com
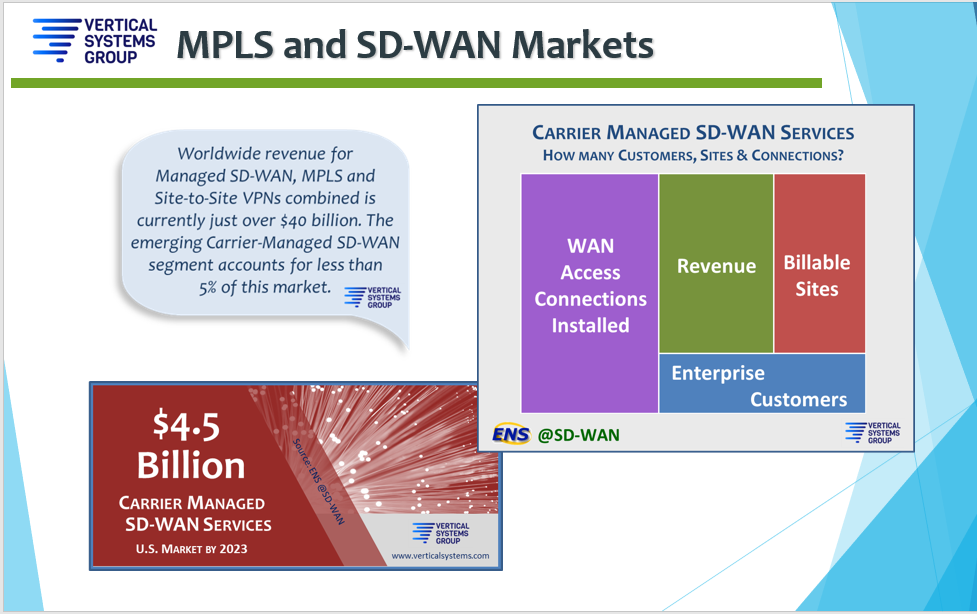
Debate Wide Area Networking As The Technology And Players Mature What S Happening With Sd Wan And Mpls Vertical Systems Group

Vpn Explained How Does Vpn Work And Why Would You Use It

Configure Fortigate Ddns With Free Ddns Service Noip Net Infosec Memo

Fortinet Fortigate Review Don T Underestimate Fortianalyzer It Can Give You A Better Understanding Of What Is Going On In Your Network It Central Station

Configure Fortigate Ddns With Free Ddns Service Noip Net Infosec Memo

Vpn Explained How Does Vpn Work And Why Would You Use It

Solved Ipsec Vpn Tunnel Between Watchguard And Fortigate Is Up Traffic One Way

Network Design Scenario 3 Remote Access Vpn Design

What Is Malware Definition Types How To Guard Fortinet

No comments:
Post a Comment