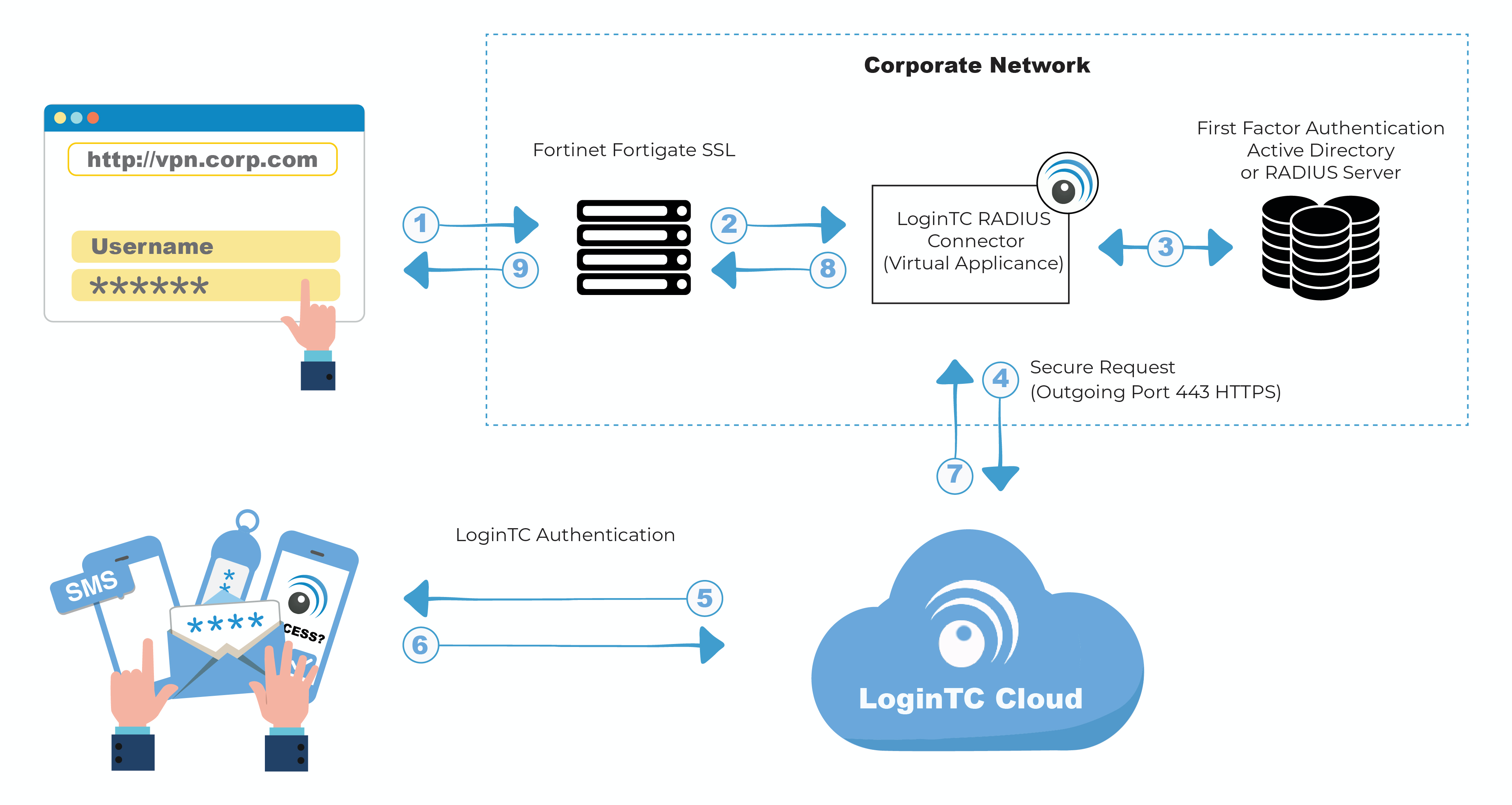
If your computer has a firewall turned on you will need to configure it to allow inbound connections. I only have one physical port available on each of the Fortigates so am trying to make use of VLANs.
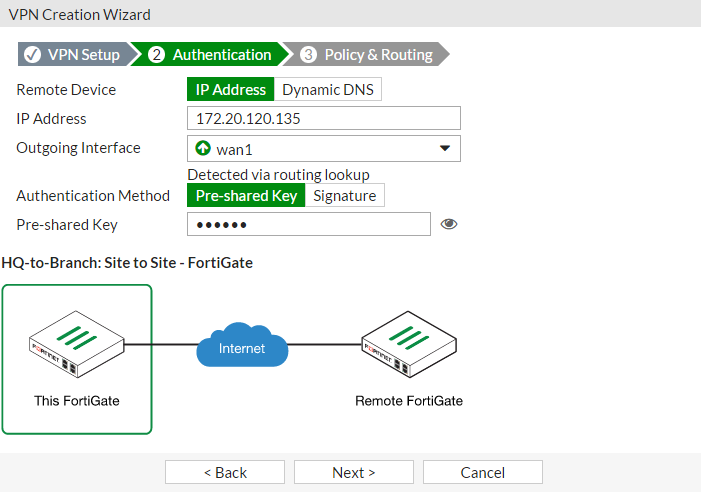
Cookbook Fortigate Fortios 5 4 0 Fortinet Documentation Library
If this is not setup properly any inbound connection of your network will fail.
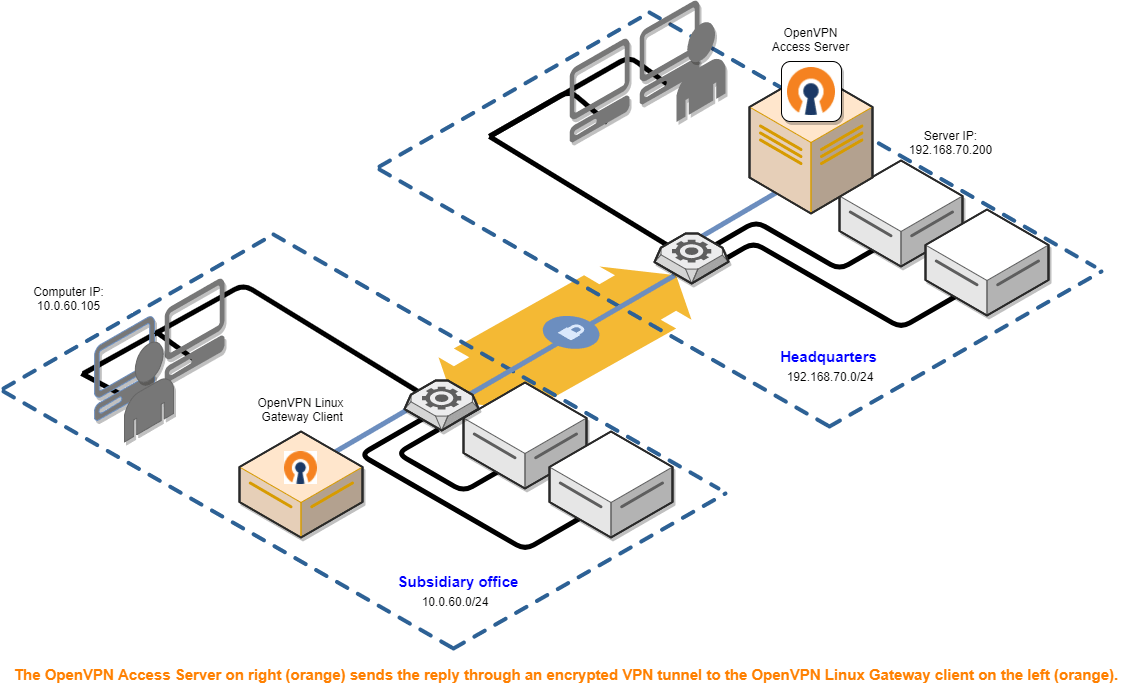
Dont just sit there start getting more vpn fortigate. Just sit back relax and continue reading the article. I have two Fortigate 1000A s that I am trying to connect over a L2 circuit. Fortunately I was able to get my hands on a Fortigate 60D.
We have another solution for you guys. The title only covers a part of my question just keeping it short. Please read carefully and understand what I am asking before posting I dont need to have what I want but it is how I want it.
In the Connection Settings section under the Server Certificate drop down select your new SSL certificate. Just sit back on your chair and try it again after a few minutes or hours in some cases. Company firewall refresh management leaning towards Cisco ASA-X which I dont want We are in the middle of some major networking changes at my company.
In more human-friendly terms it basically means that your server knows exactly what you want to do it just wont let you do it because you dont have the proper permissions for some reason. Configure the Fortigate VPN to use the new SSL certificate. The previous IT guy who created it on the Fortigate is not part of the company anymore.
Googles free service instantly translates words phrases and web pages between English and over 100 other languages. Determining whether to use a routed or bridged VPN. Now were getting somewhere.
When they dont you can go crazy trying to figure out whats wrong. As we said if the first doesnt work try this method. Verify you can ping your VPN url at this point.
Of course there are much more options to fine-tune the timers etc. Im going to skip over the IPv4 setup because theres nothing new and exciting there. Guys I am experiencing a bit of an issue.
We are an entirely Cisco company and when this. End-User Interface w RDNSS. Were having an issue with Teams calls temporarily dropping.
I dont know where to start. A user is defined as any desktop laptop printer phone tablet or other Internet-connected device operating on your. But the just listed commands are the very basic configuration steps to make it running.
See also the OpenVPN Ethernet Bridging page for more notes and details on bridging. VPN ssl Tunnel stopped working Hi all Im new to Fortinet and this position. The syntax might be out of date a bit especially since it addresses a vpn to PIX using 63 commands ASA now run up to 84 with.
But I just noticed the VPN stopped working. Further if the issue still persists dont worry. But last week we change our IP from our site to the countyI work at a school district.
Alternatively depending on the Windows OS versions the other way involves using the command prompt to resolve the issueAll a person requires is to search cmd or command in the run tab which will open up the DOS layoutIn this interface typing net stop dnscache and net start dnscache will do the refreshing of DNS files. We have an illustrated guide. When they work VPNs are great.
I have created the VLAN on each of the interfaces Int 8. Recommended User Counts The most important consideration when buying a Fortinet next-gen firewall is the number of users your network must support. Here is the first google result for fortigate to cisco vpn.
Try again after some time. Here are four of the biggest trouble areas with VPN connections and how you can fix them. Were not using DDOS protection were not accessing Teams over a VPN and were not using a proxy or proxy mode.
See FAQ for an overview of Routing vs. Overall routing is probably a better choice for most people as it is more efficient and easier to set up as far as the OpenVPN configuration itself than bridging. User counts means more than just the number of employees in your organization.
Once that was out of the way I turned my attention to getting IPv6 sorted. We have ONE WAY IPSEC tunnel on the Fortigate I just dont know how to replicate it on the Cisco FMC. If the problem is caused by the high real-time or the server side issues trying after a few moments may help you download the files without any interruptions.
For your interest this is how my IPv6-only network on a Windows 7 machine looks like with the just proposed settings. However when I pa. I cant ping our gateway but not sure if.
Among the more popular firewalls is the one built into Windows-based computers. Any give me any advice. FINDING YOUR NEXT FORTIGATE FIREWALL.
This is the easiest method that you can do. Browse to VPN SSL Settings. Im going to migrate our firewall from Fortigate 800C to Cisco FMC.
Its kind of like youre trying to get into a private event but your name got accidentally removed from the. So Ill start off with what Im actually trying to do. Im looking at setting up a connection between my.
I saw the tech tip on Fortinets kb site Most common issues with Fortigate and Microsoft Teams although those dont seem to apply to us. By Disabling the MS Internet Connection Test by using the Group Policy. And yes Fortigate do support IPv6 over PPPoE.