Both Site to site VPN and Remote access VPN are the types of VPN which stands for Virtual Private Network. Connect a Fortigate device behind a static 11 NAT to the Internet to a Google Cloud Platform GCP VPN gateway.

Implementing Vpn Split Tunneling For Office 365 Microsoft 365 Enterprise Microsoft Docs
These rules can also prevent users within the network from accessing certain sites and programs.

The important difference between vpn fortigate and google. FortiGate SWG consolidates NGFW and SWG services helping enterprises manage their network security solution with ease. A firewall is a network security solution that protects your network from unwanted traffic. Select the tunnel listed for branch_1 and select the status column.
Theres a fundamental difference between a firewall and a UTM. Really Poor SMB performance. On branch_1 go to Monitor IPsec Monitor.
Set the Authentication Method to Pre-Shared Key and enter the key. In site to site VPN IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. Firewalls block incoming malware based on a set of pre-programmed rules.
SMB transfers are slow about 2 or 3mbps. Windows 10 Always On VPN includes support for granular traffic filtering. LOCAL_LAN ---- Fortigate ----- Fiber modem ---- Internet ---- GCP VPN Gateway ----- GCP_VPC The Fiber modem is doing NAT 11 to the Fortigate DMZ Mode is called on this modem.
Interface mode is a more sophisticated and flexible method of providing connectivity between sites due in large part to its seamless integration into the Fortigates routing table. I find the Checkpoint GUI to be much more intuitive and easier adapt to for new users. Ookla speed testing on spectrum produce consistent 6025 speed results but ATT is a bit lower than 100 down but typically 100 up each test.
Difference between Fortimail and Fortigate Email filtering 20190404 225707 0 The given difference between the fortimail and the fortigate can be understood by the users easily and I was unknown to this and I got to know the basic difference between to of the modules. This means that even if. To test the VPN initiated by branch_1.
Forti net can pr ovide good service even with its individual pro ducts but tends to bundle with. In addition traffic filter policies can be applied on a per-user or group basis. Select the VPN enter the username and password then select Connect.
Set the VPN to IPsec VPN and the Remote Gateway to the FortiGate IP address. Ive followed several. A major difference between Fortinet and Checkpoint is their GUI.
One location upgraded from a 60 meg down 25 up circuit Spectrum to a 100 updown ATT circuit. With a SoC4 security processor application-specific chips and new WAN edge features the 80F series is another entry in Fortinets steady upgrade from the excellent E Series to the faster even more secure F Series firewallsThe FortiGate 80F follows in the footsteps of the FortiGate 40F FortiGate 60F FortiGate 100F. Fortinet to Fortinet 100E to 60E IPSec Tunnel gigabit connection on the 100E and 400mbit on the 60E.
Firewalls are based on the simple idea. Fortinets latest models the FortiGate 80F and 81F have just launched. Fortinet on the other hand excels in the CLI with a CiscoAvaya mixed interface and help structure.
Site-to-Site VPN is also known as Router-to-Router VPN. Specifically IPSec Tunnels can be triggered via firewall rules based policies or interface mode. One of our clients has a fortigate at 2 locations with an IPSEC tunnel between them.
It supports all proxy deployment modes and uses multiple detection techniques such as web filtering DNS filtering data loss prevention antivirus intrusion prevention and advanced threat protection to protect employees from internet threats. Have adjusted tcp-mss in the IPV4 policy for the indicated branch and on the IPSEC interface itself to 1306 which is low but higher doesnt matter when left at default. Also select appliances support clustering for increased performance VPN load balancing to optimize available resources advanced high availability configurations and more.
Much like the 40F the FortiGate 60F model is also recommended for branch offices or mid-sized businesses and offers top protection against all types of cyber threats and offers an industry-leading secure SD-WAN in a simple and easy to use solution. Where DirectAccess provides access to all internal resources when connected Always On VPN allows administrators to restrict client access to internal resources in a variety of ways. Fortinet Fortigate UTM appliances provide IPSec as well as SSL VPN out of the box.
The difference between branch_2 and branch_1 at this point is that the tunnel entry for branch-1 will not have a remote gateway IP address. Configuring the VPN overlay between the HQ FortiGate and cloud FortiGate-VM Configuring the VPN overlay between the HQ FortiGate and AWS native VPN gateway Configuring the VIP to access the remote servers Configuring the SD-WAN to steer traffic between the overlays. Beyond that the FortiGate 60F allows users to depend upon the management console.
Expand Advanced Settings Phase 1 and in the Local ID field enter dialup1. Configure remaining settings as needed then click Save. Flexible VPN capabilities include support for remote access site-to-site and clientless VPN.
A firewall merely does stateful inspection of the traffic whereas a UTM proactively stops attacks even on allowed ports because it contains the all important IPS Intrusion Prevention System. Both Cisco AS A and Fortinet FortiGate provide similar f eatures but dif fer in.
How To Set Up A Site To Site Vpn With A 3rd Party Remote Gateway

Implementing Vpn Split Tunneling For Office 365 Microsoft 365 Enterprise Microsoft Docs

Fortios 5 2 Update Ssl Vpn Configuration On Fortigate Mirazon

Cookbook Fortigate Fortios 6 2 0 Fortinet Documentation Library

Malwarebytes Vs Bitdefender Malwarebytes Firewall Security Antivirus Software

Cookbook Fortigate Fortios 6 2 9 Fortinet Documentation Library

Acronis Disaster Recovery Cloud How To Configure Acronis Ipsec Vpn Gateway And Fortinet Fortigate Next Generation Firewall Knowledge Base
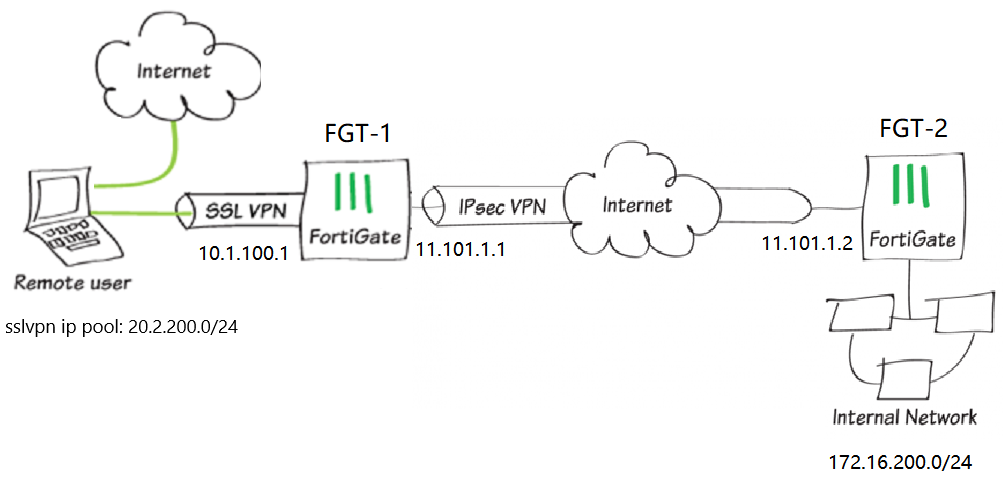
Cookbook Fortigate Fortios 6 2 0 Fortinet Documentation Library

Cookbook Fortigate Fortios 6 2 9 Fortinet Documentation Library
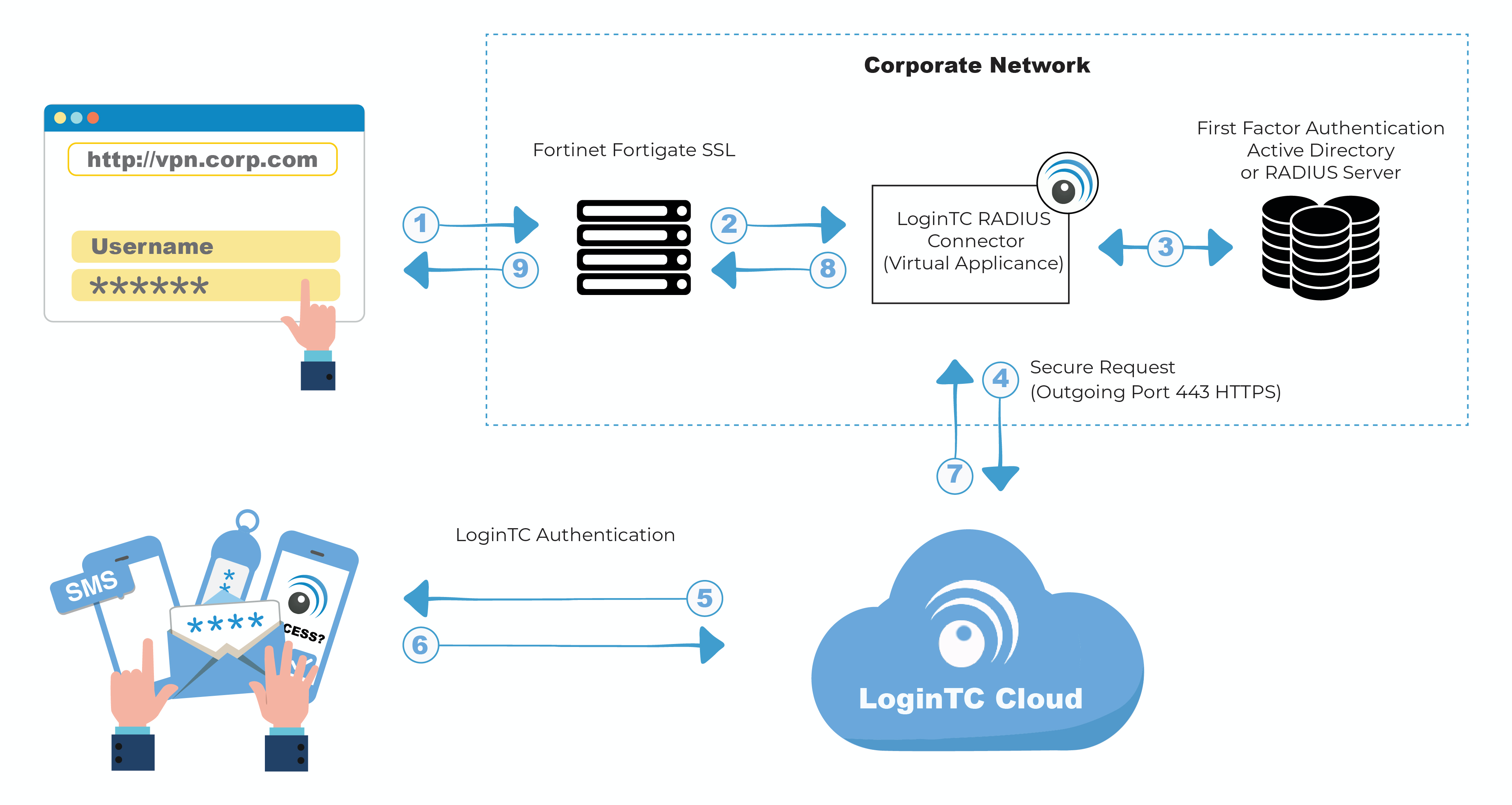
Two Factor Authentication For Fortinet Fortigate Ssl Vpn Radius 2fa

District Ssl Vpn Connection And Clients Public Space Remc1 Supportnet

Administration Guide Fortigate Fortios 7 0 1 Fortinet Documentation Library
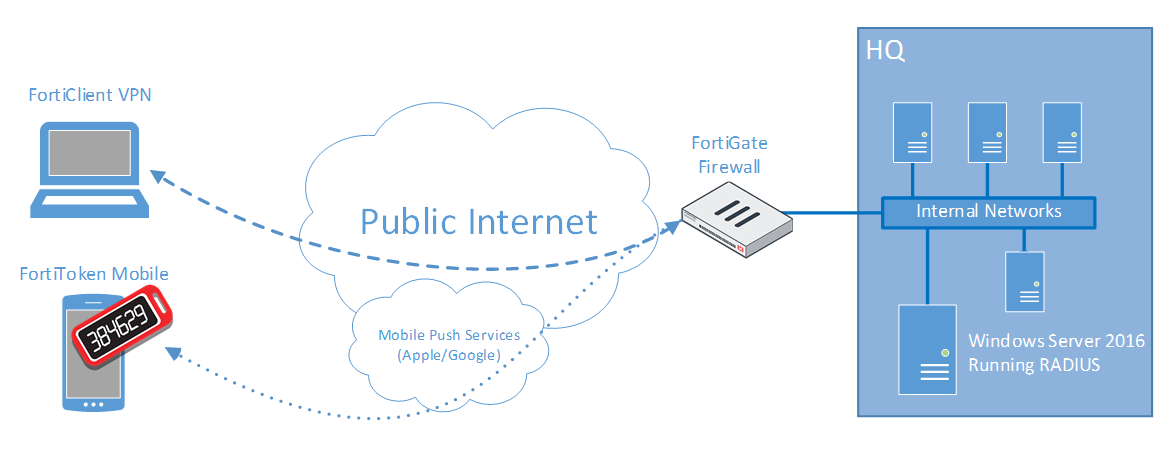
How To Setup Fortinet Multifactor Vpn Using Windows Radius Fortitoken Mobile Pliantcloud

Cookbook Fortigate Fortios 6 2 9 Fortinet Documentation Library

100 Working Hotspot Shield Vpn Unlimited Bandwidth Access For Hot Spot Best Vpn Public Network

Vpn Explained How Does Vpn Work And Why Would You Use It

Administration Guide Fortigate Fortios 7 0 0 Fortinet Documentation Library

How Do I Configure The Ssl Vpn Feature For Use With Netextender Or Mobile Connect Sonicwall

Acronis Disaster Recovery Cloud How To Configure Acronis Ipsec Vpn Gateway And Fortinet Fortigate Next Generation Firewall Knowledge Base
No comments:
Post a Comment